If you’re reading this article, you’ve probably heard of the OWASP Top 10. For those who haven’t, it’s a list of the ten most critical vulnerabilities for web applications. Injection vulnerabilities are third on this list. Some of the common examples of injection vulnerabilities include SQL injection, cross-site scripting, and command injection.
In 2023, SQL Injection vulnerabilities were ranked as the most popular vulnerability, affecting over 23% of websites and web applications worldwide (Statista). This increased popularity makes it a prime target for attackers, so every website owner needs to be aware of it. In this article, I will explore this vulnerability and what website admins and owners should do to protect their sites.
What is an SQL Injection Attack?
An SQL injection attack is a hacking technique where attackers trick a website or application into running harmful database commands. Websites that have an SQL Injection vulnerability accept input from users like in a login form and doesn’t properly check or sanitize these inputs before sending it to the database. Sanitizing means cleaning data to make it safe, correct, and free from harmful or invalid content.
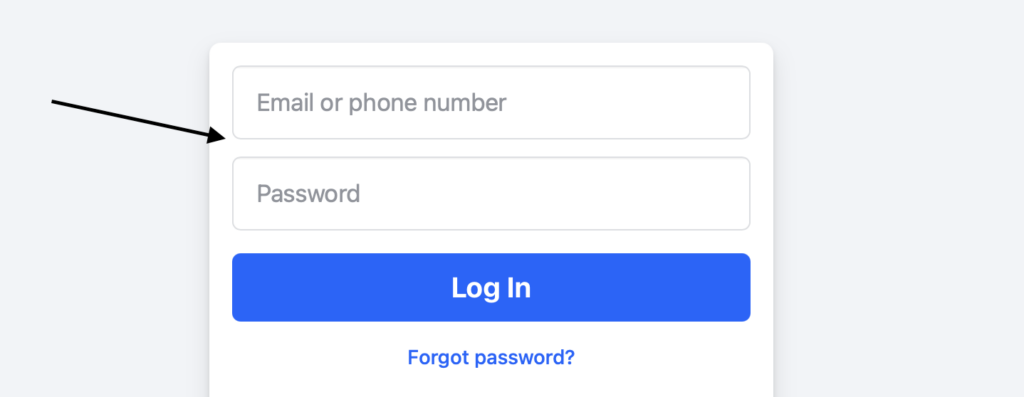
Think of it like this: if a website (like in the image above) is asking for a username and password, instead of entering their own details, an attacker sends special code designed to break into the system. If the website is not secured, the database runs this code as if it’s part of its normal operations. When this code (database querry) is run successfully, the attacker can use this vulnerability to access sensitive information in the database like passwords. The attackers can even use such information to take over the website.
Why SQL Injection is Still a Major Concern
- Persistence of Poorly Coded Applications and Databases: SQL injection attacks remain a threat because many applications are still poorly coded. This is mainly because a large number of developers often lack training in secure practices, leading to vulnerabilities, tight deadlines and shortcuts during development worsen, and legacy systems with outdated code remain.
- Common Misconceptions About Security Measures: Many believe HTTPS makes their websites or web apps secure, including protecting them against Injection attacks. However, it is important to remember that HTTPS only encrypts data during transmission and doesn’t protect any data at rest, including that in the database. It is crucial to consider all security measures to protect data both while it is stored and during its transfer.
- Potential Impact of a Successful SQL Injection Attack: Successful SQL injection attacks lead to severe consequences, such as data breaches exposing customer information, financial losses from lawsuits and fines, and damage to an organization’s reputation. Attackers can also use information stolen from the database to take over the website, which can disrupt operations.
Real-World Examples of SQL Injection Attacks
- Heartlant (2008): Heartland Payment Systems, a payment processor, suffered a massive SQL injection attack that led to over $130 million in losses. The attackers managed to steal 130 million credit card numbers, making it one of the largest data breaches involving credit card information in history. (Read more about the Heartland attack).
- Multisite Attack (2014): In this attack, Russian hacker group used SQL injection to collect over 1.2 billion unique IDs and password combinations from more than 420,000 websites worldwide. (Read more about this attack)
- TalkTalk (2015): TalkTalk, a UK telecom giant, faced severe criticism after an SQL injection attack compromised personal information of hundreds of thousands of customers. (Read more about the TalkTalk attack)
- Epic Games (2016): Epic Games fell victim to an SQL injection attack targeting their forums, exponsing 800,000 user accounts. This attack was linked to vulnerabilities in vBulletin, a popular but notoriously insecure message board software (Read more about the Epic 2016 attack).
Best Practices to Prevent SQL Injection Attacks
- Input Validation and Sanitization: Validating and sanitizing user inputs ensures that only expected and safe data reaches the database. Ensuring that all inputs are clean and sanitized is the most reliable strategy for preventing SQL Injection attacks. For example, if an input form on a webpage expects a numeric value, any non-numeric input should be rejected. This step prevents attackers from injecting malicious code by treating all user input as untrusted and verifying it before processing.
- Prepared Statements and Parameterized Queries: Prepared statements and parameterized queries are the gold standard for preventing SQL injection. Unlike traditional SQL queries, Prepared Statements and Parameterized Queries separate code and data to ensure user inputs are treated as data, not executable commands. This approach makes it impossible for malicious inputs to alter the query structure, even if they include harmful SQL code.
- Using ORM (Object-Relational Mapping): ORM tools like Hibernate, Django ORM, or SQLAlchemy act as a bridge between the database and object oriented programming languages like Python and Java. These tools automatically use parameterized queries, further reducing the risk of SQL injection. By using ORM tools, developers can interact with the database without writing raw SQL in their backend code, making applications more secure and easier to maintain. In addition to security, ORMs improve code readability and maintenance, support multiple databases with minimal changes, and make complex query handling easier through intuitive methods.
- Web Application Firewalls (WAFs): A WAF sits between the websever and the client (user browser), acting as a shield by filtering malicious traffic before it reaches the application. Since the WAF operates at the application layer of the OSI model, it analyzes HTTP/HTTPs requests and not just the IP addresses or network metadata. Modern WAF analyze incoming requests and block all traffic that has patterns that resemble SQL injection attacks. This can partially help safeguard your web app even if its code has some injection vulnerabilities.
- Database Permissions: Limiting user privileges in the database minimizes the potential damage of an SQL injection attack. For example, application users should only have access to the data and commands they need, such as restricting the ability to drop tables or modify schema. This reduces the attack’s blast radius if a vulnerability is exploited.
- Regular Security Audits: Regular security practices like code reviews, penetration testing, and vulnerability scans help identify and fix vulnerabilities before attackers can exploit them. SonarQube can be used for code reviews, Burp Suite and OWASP ZAP for pen testing and vulnerability scanning. These audits ensure that applications follow secure coding standards and that any new vulnerabilities introduced over time are promptly addressed.
Key Takeaway
SQL injection is still a major threat to web applications, even with improvements in security. To protect against this attack, website owners and developers should focus on understanding its basics and implementing strong security measures. Key steps include prioritizing input validation, sanitization, and using parameterized queries.
Additional safeguards, such as deploying Web Application Firewalls (WAF) and limiting users to the minimum privileges needed for the database, can also help reduce the risk of SQL injection. It’s important to ensure that all members of the design and deployment teams are familiar with the best coding practices to avoid errors due to lack of awareness.